Technical Surveillance Countermeasures TSCM Bug Sweep Services
Has a situation gotten out of hand?
Do people know things they shouldn't?
Do you suspect that your privacy is being violated?
If you suspect your privacy is being violated, a TSCM Bug Sweep will give you the knowledge and peace of mind to move forward in 2023

Glen Bass Investigations specializes in detecting and revealing eavesdropping devices
Contact us today for more information
952-200-5755
What is TSCM Corporate Bug Sweep Services?
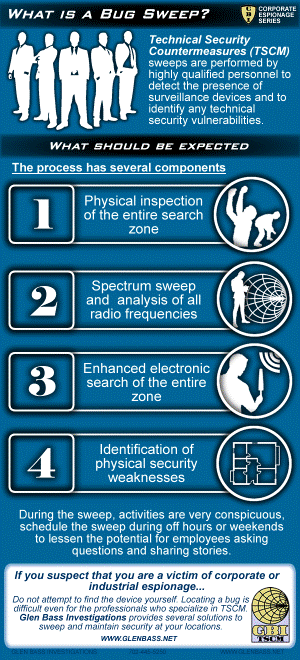
A Technical Security Countermeasures (TSCM) sweep has several components
- Physical inspection of the entire search zone
- Rf spectrum sweep and analysis of all radio frequencies
- Enhanced electronic search of the entire zone
- Identification of physical security weaknesses
A TSCM bug sweep services are very conspicuous, schedule during off hours or weekends
Our privacy is a part of our lives that each of us hold dear. When our privacy is threatened it can be not only personally hurtful but potentially devastating to our business and social relationships as well as our most treasured family matters.
Once we suspect that our privacy has been violated in a nefarious way, finding comfort or peace of mind can be difficult if not impossible.
Glen Bass Investigations [GBI] specializes in TSCM Bug Sweeps for Corporate, Industrial and Residential properties. Contact us to learn more today.

Sweep My Ride
ANNOUNCING!!!!
Sweep My Ride is a facility dedicated to detecting and locating hidden electronic devices on vehicles
"Sweep My Ride" is an extension of Glen Bass Investigations (GBI). In GBI's experience providing business and residential TSCM sweeps, requests for vehicle sweeps are on the increase. The GBI process for sweeping vehicles has been developed from over 20 years experience on virtually all types of vehicles.
SWEEP MY RIDE FACILITIES AND TECHNIQUES ARE A UNIQUE COMBINATION OF TECHNOLOGY, TRAINING AND YEARS OF EXPERIENCE

TSCM Team Methodology
The GBI team has been providing Technical Surveillance Countermeasures (TSCM) services for over 15 years and have, over time and tested experience developed a complete and thorough method for sweeping a space both physically and electronically.
Scanning for RF signals is only one part of an effective TSCM sweep, a physical inspection of ceiling spaces, walls, outlets, IT & TELCO equipment as well as any conditions that may be present due to architectural or production floor features.
A TSCM Investigator will visit your site to establish the physical construction of your space, the scope of your needs and provide a proposal for corporate bug sweep services based upon what we learn.

Military Grade Equipment
A TSCM Bug Sweep is also known by the reference of "Bug Sweeps", and the more modern name of Electronic Eavesdropping Detection or EED.
GBI's TSCM Investigators are Certified Specialists in the detection and locating of eavesdropping devices. Our Team is trained to the same specifications and utilizes the same equipment and techniques used by federal government.
We use the state of the art OSCOR, an R.F. Spectrum Analyzer, as well as F.L.I.R., telephone and networks analyzers ($100,000).
Counter Surveillance Security Programs
Safe Room Service
We provide a Safe Room Service, where a TSCM Investigator will come in just prior to your meeting, set up our equipment, both Spectrum Analyzers and Acoustic Noise Generators, conduct a preliminary bug sweep and stay to ensure no information is leaked or broadcasted.
Quarterly TSCM Sweeps
Continuing security and maintenance of your security position requires re-sweeping a location on unannounced regular intervals. Our process marks previously cleared outlets and electrical equipment which dramatically reduces the cost of follow up visits.
Corporate Espionage Series (CES)
CES provides easy steps to better protect your organizations privacy
If you suspect that you are a victim of corporate or industrial espionage
Restrain yourself from attempting to find a device yourself, detecting bugs is difficult even for the professionals who specialize in TSCM
A Technical Surveillance Countermeasures (TSCM) sweep is a service provided by highly qualified personnel to detect the presence of surveillance devices and to identify technical security vulnerabilities of the site in question.
GBI uses proven technique & decades experience in Counter-Surveillance & Technical Security Counter Measures (Bug Sweeps) to secure our clients locations
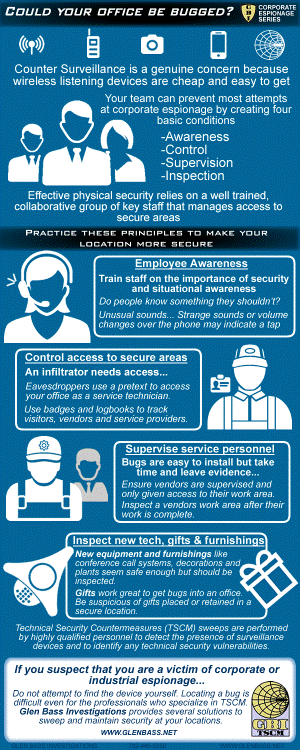
Prevent Eavesdropping and Protect Privacy
Protection against the installation of eavesdropping devices or "Bugs"require
- Awareness: Train staff on the importance of security and situational awareness
- Control: Control access to secure areas with visitor badges and logbooks
- Supervision: Bugs take time to install, supervise service personnel
- Inspection: Inspect new technology, gifts and furnishings
If you suspect your office is bugged
Report your concerns to the appropriate team member
- Step #1: Notify corporate security in person, not by telephone or email
- Step #2: Only discuss your concerns with those who have a need to know
- Step #3: Avoid discussing the issue in a potentially bugged area
- Step #4: Discontinue important discussions in suspected areas until they are cleared
What is Technical Surveillance Countermeasures TSCM?
The systematic physical and electronic examination of a designated area by properly trained, qualified and equipped persons in an attempt to discover electronic eavesdropping devices, security hazards or security weaknesses
Minnesota Bug Sweep Services
A Corporate Bug Sweep systematically locates and identifies electronic devices intended to eavesdrop on private communications
The GBI team has over 20 years experience in providing high level TSCM bug sweep services to corporations facing complicated security concerns.
In Minnesota as in most states, you need to be a licensed Private Investigator to conduct a corporate bug sweep. We are licensed to do so, which allows us to do compete consulting work while protecting your interests. We operate the latest REI counter-eavesdropping equipment and can ensure complete confidentiality.
We protect your confidentiality and ensure that your business remains your business
Professional bug sweeping services do not just wave an antenna wand around and declare that a site is free from “Bug Surveillance”
Bug sweep detection services use very expensive equipment and while a person can purchase a “bug sweeping device” from the internet and call themselves a “Professional Bug Sweeper”, in fact, providing “surveillance and counter surveillance” is work that must be done by a licensed private investigator. An investigation will usually be conducted in layers.
Bug sweep services cost
Several considerations go into price estimating a business bug sweep an industrial bug sweep or a residential bug sweep and can vary greatly from site to site. Some of the conditions that affect pricing include, but are not limited to:
- Nature of the threat: Whom is suspected of eavesdropping?
- Age of the Structure: Is it New or Old construction?
- Type of Construction: Business or Residential?
- How big are the spaces: High Ceilings with clean cubicles or small offices packed with electronics?
- Network and Communications: Is cabling installed cleanly or is old wiring bundled in the ceiling?
- Accessibility and Clutter: Is the space consumed by clutter, such as stacks of paper, furniture, toys, etc…?
- Square Footage: How big is the space?
Type of construction, clutter factor and square footage of a site have the greatest impact on price.
Costs can range from as high as $2.00 sq/ft to just under $1.00 sq/ft depending upon many of the conditions listed above.
Contacting a bug sweep services near you may be a bit uncomfortable, sometimes articulating concerns about eavesdropping and espionage can be difficult. Professional bug sweeping services should understand this and be able to explain the process, the timeline and what cost you should expect.
Radio Frequency Analysis
Counter-surveillance companies, companies that sweep for listening devices, use a Technical Surveillance Countermeasures device known as a Spectrum Analyzer which serves as the backbone for a team’s electronic bug detection services. This bug sweeping device is used with other tools such as the REI ANDRE which is used to pinpoint bugs and transmitting electronics.
Our team uses the ANDRE to scan the RF spectrum. It’s a hand-held broadband receiver that detects and assists in locating nearby RF, infrared, visible light, carrier current and other types of transmitters.
These and many other electronic instruments are used to validate and verify signals when they are detected throughout the electronic spectrum as high as 24Ghz.
Las Vegas Bug Sweep Services
Experience matters, our team members have been providing TSCM sweep services in Las Vegas for over 20 years.
Our reputation speaks for itself, that is why our team is the most highly recommended TSCM Bug Sweep (Corporate Bug Sweep) services in Las Vegas
Share on Facebook Share on LinkedIn
TSCM "The systematic physical and electronic examination of a designated area by properly trained TSCM Investigators in an attempt to discover electronic eavesdropping devices, security hazards or security weaknesses."